Content Authenticity and Provenance — Ancon Protocol is ready to end NFT forgeries
We achieved something we thought was pretty difficult to apply without resorting to bare mobile development, hardware purchases and specialized blockchain nodes. All this in a few weeks.
Let’s go through each step of how it works with du. app
Connect to a blockchain network
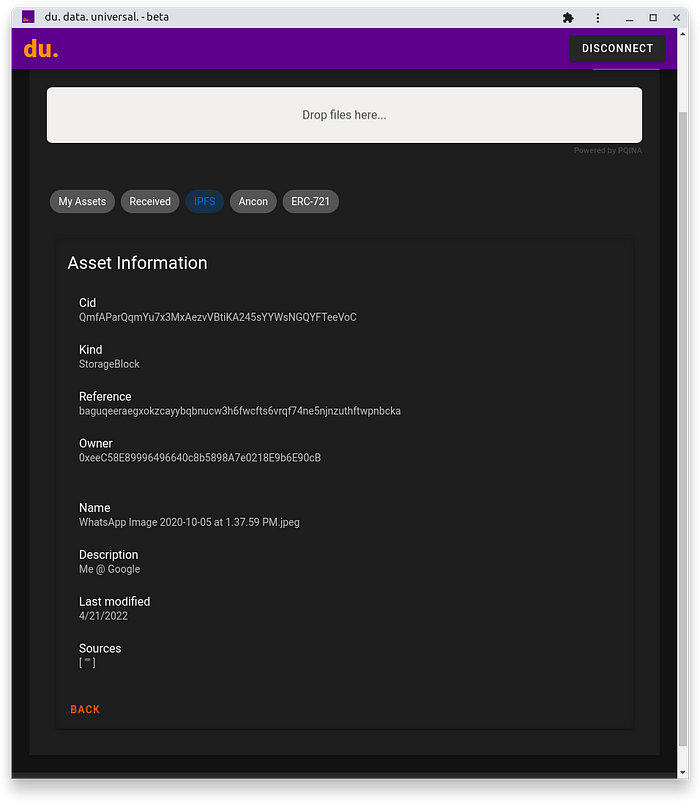
Upload a file to ParkyDB storage or IPFS compatible

Sign image using Ancon Protocol Content Authenticity service


Share with Whatsapp or IPFS, and obtain the Cid hash, we’ll do this to review the technical aspects
Technical explanation
W3C WebAuthn
a) WebAuthentication signs using a keypair bound to a domain. In this case du.xdv.digital. Any signature will be only verifiable for that specific domain and set of keys (or smartphones) owneed by someone. Someone in du. app is an user connected with an address from a WalletConnect wallet.
The DAG block as JSON in top left has the image which has Exif data (or later in the future CAI Jumbf boxes), top right is the StorageAsset data, and bottom left the image.
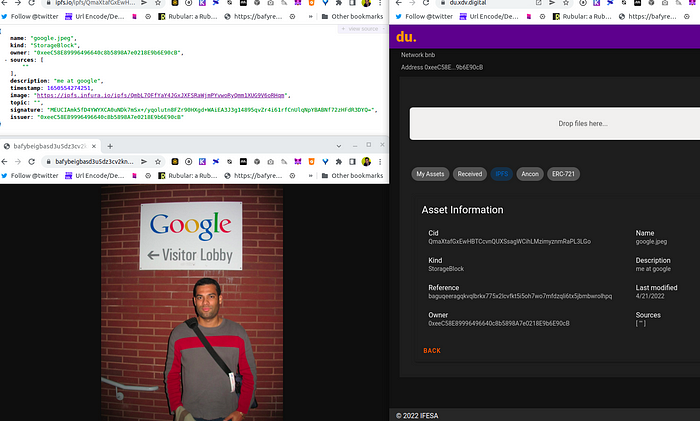
Image Exif / Jumbf Box
As many might recognize, the Exif data we are using just a few fields, where the Author represents a DID or EVM Address (secp256k1). This is very important to know, WebAuthn signs using secp256r1 or NIST P-256.

Verified Credentials
The Copyright field contains a did-jwt NIST P-256 signed output. The secret sauce is that we have used Verified Credentials with JPEG assets, which we could further enhance into VC Issuer — Holder — Verifier flow.

Extensible by default
- Any cryptographic hardware is supported: PKCS11 (Qualified Signatures), PKCS12, WebAuthn, Ledger, Trezor, Yubi HSM. You could batch content authenticate image assets before tokenizing.
- du. app only works for desktop with WebAuthn in any platform. Built in support works for PWA mobile, but the current configuration is all or nothing. Likely if this is required for any business we can give them support and implementation.
- Ancon Protocol offchain ICS23 proof signatures is the cherry on top. Yubico recommends that authenticatorData and clientDataJSON must be stored for auditing and validation purposes (which is not illustrated here).
- Which means if you get our professional services, you’ll get the first end to end, blockchain verifiable, content authenticity verifiable solution to mitigate NFT plagiarism and fakes.
- And of course this would work for similar data economy scenarios: diplomas, licenses, etc… anything currently possible in the Verified Credential and NFT use cases. Of course don’t recommend to use it for DeFi assets, for that there is already a ton of technology proven and useful.
Hope you like this entry, I very much did, considering I was planning to make these features for 2023!
Regards
— IFESA
